Managing software license keys might seem like a routine IT chore, but the numbers tell a different story. A staggering 57 percent of organizations pay for software they no longer use, leading to massive waste and compliance risks. Most people assume buying an extra license or two is harmless. The real issue is that unchecked license sprawl can quietly drain budgets and leave organizations wide open to security headaches.
Table of Contents
ToggleQuick Summary
| Takeaway | Explanation |
|---|---|
| Implement Strong Access Controls | Establish strict protocols to limit license key access to authorized users only. This prevents unauthorized usage and ensures compliance with licensing agreements. |
| Optimize License Usage to Avoid Overprovisioning | Regularly track and assess software license usage to avoid unnecessary expenses due to excess licensing that organizations do not utilize fully. |
| Invest in Centralized Management Tools | Use centralized tools for effective license tracking, resource management, and compliance monitoring to streamline operations across departments. |
| Secure Key Distribution and Storage | Utilize encrypted and automated methods for distributing and storing license keys to enhance security and reduce risks of unauthorized access. |
| Conduct Regular Audits and Reviews | Implement periodic audits of access permissions and usage patterns to ensure ongoing compliance and identify potential security vulnerabilities. |
Understanding License Key Management Systems
License key management systems represent critical infrastructure for organizations seeking to control and optimize their software asset utilization. These sophisticated platforms enable businesses to track, deploy, and validate software licenses across complex technological ecosystems.
Core Components of License Key Management
To provide a clear overview of the main technological and administrative elements essential to effective license key management, the following table summarizes the core components discussed in this section:
| Component | Description |
|---|---|
| Centralized Repository | Secure database that stores all license information, including purchase dates and usage permissions |
| Authentication Mechanisms | Verification processes to ensure only authorized users can access, modify, or generate license keys |
| Compliance Tracking | Automated monitoring of license usage to ensure adherence to contractual and organizational requirements |
| Role-Based Access Control | Assigns permissions based on user roles and responsibilities, improving security |
| Audit Logging | Tracks and records all interactions with license keys for compliance and security review |
At its fundamental level, a license key management system encompasses several essential technological and administrative components. The National Institute of Standards and Technology (NIST) recommends a comprehensive approach that integrates multiple layers of security and organizational control.
Key architectural elements include:
- Centralized Repository: A secure database housing all license information, tracking purchase dates, expiration timelines, and specific usage permissions.
- Authentication Mechanisms: Robust verification protocols ensuring only authorized personnel can access, modify, or generate license keys.
- Compliance Tracking: Automated systems monitoring license utilization against contractual agreements and organizational entitlements.
The primary objective of these systems extends beyond mere record-keeping. They serve as strategic tools for preventing unauthorized software usage, managing compliance risks, and optimizing software investment strategies.
Technological Challenges in License Key Management
Managing license keys presents complex technological challenges that require advanced strategic approaches. According to Centers for Medicare & Medicaid Services (CMS), implementing robust key management involves sophisticated Role-Based Access Control (RBAC) mechanisms and comprehensive auditing infrastructures.
Organizations must navigate intricate requirements such as:
- Dynamic credential management
- Secure credential rotation
- Comprehensive logging and tracking
- Real-time compliance monitoring
These challenges demand not just technological solutions but also well-defined organizational policies and systematic implementation strategies. Effective license key management transcends simple tracking mechanisms, representing a critical intersection of technological governance, financial optimization, and regulatory compliance.
By implementing sophisticated license key management systems, organizations can transform potential administrative burdens into strategic advantages. These platforms provide granular visibility into software assets, enable precise cost control, and mitigate potential legal and financial risks associated with improper software licensing.
The evolution of cloud computing, software-as-a-service models, and increasingly complex licensing frameworks continues to reshape the landscape of license key management. Organizations must remain adaptive, leveraging advanced technological solutions that offer flexibility, security, and comprehensive oversight of their software ecosystem.
Common Challenges When Managing License Keys
Managing software license keys presents organizations with a complex array of technological and administrative challenges that can significantly impact operational efficiency and financial performance. These challenges extend far beyond simple tracking mechanisms, requiring sophisticated strategies and robust technological solutions.
Overprovisioning and Unnecessary Licensing Costs
One of the most critical challenges in license key management is the persistent issue of overprovisioning. According to a GovLoop media survey, 57% of organizations pay for software that is no longer in use, and an equivalent percentage maintain more licenses than necessary. This inefficiency translates into substantial financial waste and represents a significant operational blind spot.
The root causes of overprovisioning include:
- Lack of Usage Tracking: More than 33% of organizations do not effectively monitor software usage or are unaware of their tracking capabilities.
- Decentralized Procurement: Multiple departments purchasing licenses without centralized oversight.
- Automatic Renewal Contracts: Perpetual agreements that continue regardless of actual software utilization.
Scalability and Administrative Complexity
TechTarget experts emphasize that key management does not inherently scale well in enterprise environments. Manual tracking becomes increasingly problematic as organizational complexity grows. The ideal key management system must seamlessly integrate with existing infrastructure while providing straightforward administration, secure key delivery, and reliable recovery mechanisms.
Technological challenges in scaling license key management include:
- Complex authentication protocols
- Distributed software environments
- Varying license model complexities
- Dynamic workforce and software usage patterns
Effective management requires sophisticated technological solutions that can adapt to rapidly changing organizational needs. Learn more about resolving common licensing challenges to minimize operational disruptions.
The evolving landscape of software licensing demands a proactive, strategic approach. Organizations must invest in advanced license key management systems that provide real-time visibility, automated tracking, and comprehensive compliance monitoring. By addressing these challenges systematically, businesses can transform potential administrative burdens into strategic advantages, optimizing their software investments and maintaining regulatory compliance.
Ultimately, successful license key management is not just about tracking numbers but about creating a holistic, intelligent approach to software asset management. It requires continuous adaptation, robust technological infrastructure, and a commitment to financial and operational excellence.
Best Practices for Secure and Efficient Handling
Effective license key management requires a strategic approach that prioritizes security, efficiency, and comprehensive organizational control. By implementing robust practices, businesses can minimize risks, optimize software asset utilization, and maintain regulatory compliance.
Implementing Strong Access Control Mechanisms
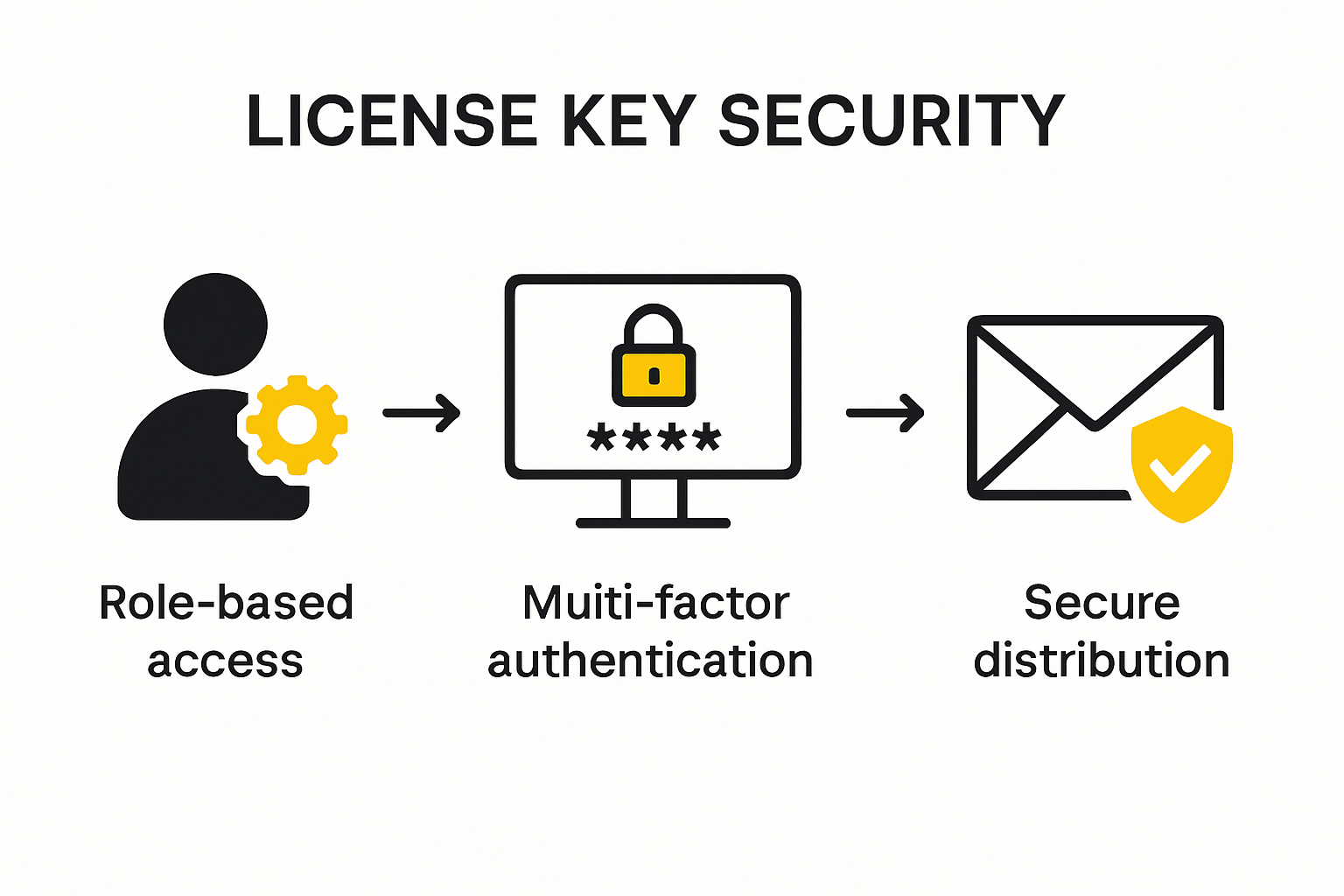
The CMS Key Management Handbook emphasizes the critical importance of establishing rigorous access control protocols. Organizations must develop a comprehensive framework that restricts license key access to authorized personnel through sophisticated authentication mechanisms.
Key strategies for access control include:
- Role-Based Permissions: Implementing granular access levels that align with specific organizational roles and responsibilities.
- Multi-Factor Authentication: Requiring multiple verification steps to prevent unauthorized key access.
- Regular Access Audits: Conducting periodic reviews to validate and update user permissions.
Secure Key Distribution and Storage
SSL.com’s guide on key management recommends advanced protocols for secure key distribution and storage. Organizations must move beyond manual transfer methods and leverage automated secure protocols.
Critical recommendations from security experts include:
- Automated Secure Protocols: Utilizing TLS and other encrypted transfer mechanisms
- Cryptographic Module Storage: Implementing Hardware Security Modules (HSMs) for isolated key protection
- Encryption at Rest: Ensuring software keys are encrypted when not actively in use
Fortanix security recommendations further emphasize the importance of comprehensive key management strategies. The use of secure APIs like the Key Management Interoperability Protocol (KMIP) provides an additional layer of security and standardization in key distribution processes.
Regular audit trails and comprehensive logging become crucial components of an effective license key management strategy. These mechanisms enable organizations to track key usage, detect potential unauthorized activities, and maintain a clear record of all interactions with critical software assets.
Organizations must also develop robust disaster recovery and key rotation strategies. This involves creating secure backup mechanisms, establishing clear protocols for key replacement, and ensuring continuity of software access during potential security incidents.
The landscape of license key management continues to evolve, driven by increasing complexity of software ecosystems and heightened security requirements. Successful implementation requires a holistic approach that combines technological solutions, clear organizational policies, and a proactive security mindset.
Ultimately, best practices in license key management are not about implementing a static set of rules, but creating a dynamic, adaptive system that can respond to changing technological and security landscapes. Organizations must remain vigilant, continuously reassessing and improving their key management strategies to protect their critical software assets.
Choosing the Right Tools for Your Organization
Selecting appropriate license key management tools represents a critical strategic decision that can significantly impact an organization’s operational efficiency, financial performance, and regulatory compliance. The right technological solution transforms license management from a complex administrative burden into a streamlined, intelligent process.
Critical Evaluation Criteria for License Management Tools
The following table organizes the key evaluation criteria that organizations should use when selecting license key management tools, helping compare what features are most essential:
| Evaluation Criteria | Purpose or Benefit |
|---|---|
| Automation Capabilities | Automatic tracking of usage, renewal alerts, and compliance monitoring |
| Integration Flexibility | Ensures compatibility with existing IT infrastructure and software |
| Reporting & Analytics | Provides detailed insights into license utilization and optimization |
| Centralized Management | Offers hierarchical control and visibility across all software assets |
| Documentation | Maintains detailed records of licenses, contracts, and software assets |
Faronics experts emphasize the importance of implementing management tools that provide comprehensive automation and insightful tracking capabilities. Organizations must carefully evaluate potential solutions across multiple dimensions to ensure alignment with their specific technological ecosystem and business requirements.
Key evaluation criteria include:
- Automation Capabilities: Tools that automatically track usage patterns, generate renewal alerts, and provide compliance monitoring
- Integration Flexibility: Seamless compatibility with existing IT infrastructure and software environments
- Reporting and Analytics: Robust reporting mechanisms that offer granular insights into license utilization and potential optimization opportunities
Centralized Resource Management Strategies
Google Cloud recommends implementing a centralized approach to resource management that extends directly to license key tracking. This strategy enables organizations to create hierarchical management structures that provide enhanced control, visibility, and compliance monitoring.
Essential centralization features to consider:
- Hierarchical access control mechanisms
- Standardized configuration settings
- Comprehensive visibility across software asset portfolios
Documentation and Inventory Management
USU Software highlights the critical importance of comprehensive documentation and systematic inventory management. Successful license key management tools should provide robust capabilities for:
- Detailed software asset cataloging
- Transparent contract and licensing documentation
- Historical usage tracking and trend analysis

Explore our guide on streamlining license management to understand how advanced tools can transform your organizational approach.
The ideal license management solution transcends mere tracking functionality. It should serve as a strategic asset that enables proactive decision making, cost optimization, and continuous compliance monitoring. Organizations must view these tools not as expenses, but as investments in operational intelligence and financial efficiency.
As software ecosystems become increasingly complex and dynamic, the role of sophisticated license key management tools becomes more critical. Businesses must adopt solutions that offer flexibility, advanced analytics, and seamless integration capabilities. The most effective tools will provide not just tracking mechanisms, but actionable insights that drive strategic software asset management.
Ultimately, choosing the right license key management tool requires a holistic approach. Organizations must balance technological capabilities, cost-effectiveness, scalability, and alignment with broader IT strategy. Continuous evaluation and adaptation remain key to maintaining an effective license management infrastructure.
Frequently Asked Questions
What are the best practices for managing software license keys?
Effective best practices include implementing strong access control mechanisms, optimizing license usage to avoid overprovisioning, investing in centralized management tools, securing key distribution and storage, and conducting regular audits and reviews.
How can I prevent overprovisioning of software licenses?
To prevent overprovisioning, regularly track and assess software license usage, monitor renewal contracts closely, and ensure centralized procurement to avoid multiple departments purchasing licenses independently.
What components should a license key management system have?
A license key management system should have core components such as a centralized repository, authentication mechanisms, compliance tracking, role-based access control, and audit logging to facilitate effective management and security.
How do I choose the right license management tools for my organization?
When choosing license management tools, evaluate them based on criteria such as automation capabilities, integration flexibility, reporting and analytics features, centralized management functionality, and thorough documentation capabilities.
Tired of License Key Headaches? Make Software Management Effortless
If uncertainty about software compliance or wasted licensing costs keeps causing stress, you are not alone. As highlighted in this article, managing license keys can quickly become overwhelming without strong access controls, reliable distribution, and constant usage tracking. This often leads to overprovisioning and missed savings. You want instant access, total authenticity, and complete peace of mind with your licenses.
Choose a smoother path today. At Logkeys.com, you get genuine, secure Windows product keys delivered instantly, helping you avoid the pain points of unreliable vendors or chaotic spreadsheets. Start enjoying optimized license management and dedicated 24/7 support by visiting our Windows license store and learn how easy it is to secure and activate your essential software. Now is the time to streamline your operations and gain confidence with every purchase.